What is GCC High?
Microsoft created GCC High to meet the needs of the Department of Defence and Federal contractors that needed to adhere to the rigid cybersecurity and compliance requirements of NIST 800-171, FedRAMP High, and ITAR, or who need to manage CUI.
GCC High is a copy of the government commercial cloud environment but the security compliances are higher with GCC High and there are fewer Microsoft features as these do not meet compliance requirements. The data centers are only located in the United States.
Security Information
Office 365 GCC High and DoD meet the security certifications and accreditations as follows:
- The Federal Risk and Authorization Management Program at FedRAMP High, including those security controls and control enhancements as outlined in the National Institute of Standards and Technology (NIST) Special Publication 800-53.
- Microsoft 365 DoD: The security controls and control enhancements for the United States Department of Defense Cloud Computing Security Requirements Guide (SRG) for information up to Impact Level 5 (L5).
Eligibility Criteria
GCC High is reserved for the Defense Industrial Base (DIB), DoD contractors, and Federal Agencies. Every customer hoping to move to GCC High must first receive validation from Microsoft.
To gain access, there are stringent background checks for employees and any staff member requesting temporary permission. Microsoft 365 staff do not have access to GCC High and DoD environments.
| U.S Citizenship | Verification of U.S citizenship |
| Education Verification | Verification of highest degree attained |
| Social Security Number (SSN) Search | Verification that provided SSN is Valid |
| Criminal History Check | 7-year criminal record check for felony and misdemeanor offenses at the state, county, and local level and at federate level |
| Office of Foreign Assets Control List (OFAC) | Validation against the Department of Treasury list of groups with whom U.S. persons are not allowed to engage in trade or financial transactions |
| Bureau of Industry and Security List (BIS) | Validation against the Department of Commerce list of individuals and entities barred from engaging in export activities |
| Office of Defense Trade Controls Debarred Persons List (DDTC) | Validation against the Department of State list of individuals and entities barred from engaging in export activities related to the defense industry |
| Fingerprinting Check | Fingerprint background check against FBI databases |
| Department of Defense IT-2 | Staff requesting elevated permissions to customer data or privileged administrative access to Dept of Defense SRG L5 service capacities must pass Department of Defense IT-2 adjudication based on a successful OPM Tier 3 investigation |
(Table taken from Microsoft).
Migrating to/from GCC High
Migrating to GCC high will depend on a number of factors. This could be if your organization needs to handle CUI and if so, the amount of existing CUI that will need to be migrated.
CloudM Migrate Self-Hosted is suitable for this. With an on-premise instance or cluster of CloudM Migrate servers in your source network only licensing information is passed externally to CloudM.
Any data that is migrated will remain in your network, come across a CloudM server, and then out of your network into GCC High. The data stream is encrypted end to end including while on CloudM server drives.
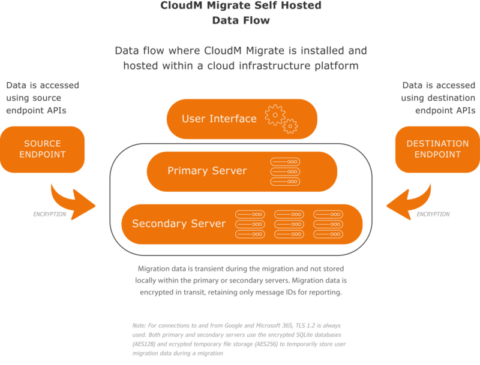
Secondary servers perform the actual migration of data from the source endpoint to the destination endpoint. They are controlled by the primary server. Multiple secondary servers can be incorporated to provide scalability for migrations requiring additional threads to increase throughput or migrate large numbers of items. Secondary servers are installed within the same network as the Primary server, whether that be on a migration farm built within your own network infrastructure or built on Google Cloud Compute, Microsoft Azure, or Amazon EC2.
Communication between primary and secondary servers is not encrypted as they should be built within the same network infrastructure. The communication between primary and secondary servers contains no user data and is only used to provide command and control.
Both primary and secondary servers communicate with the CloudM Migrate Self-Hosted licensing server using HTTPS (TLS 1.2) encryption.
If you are looking to securely migrate to or from GCC high server, contact CloudM today. Our deployment team can guide you through the process whilst ensuring security is at the center of your migration.








